How it Works?
Methodology
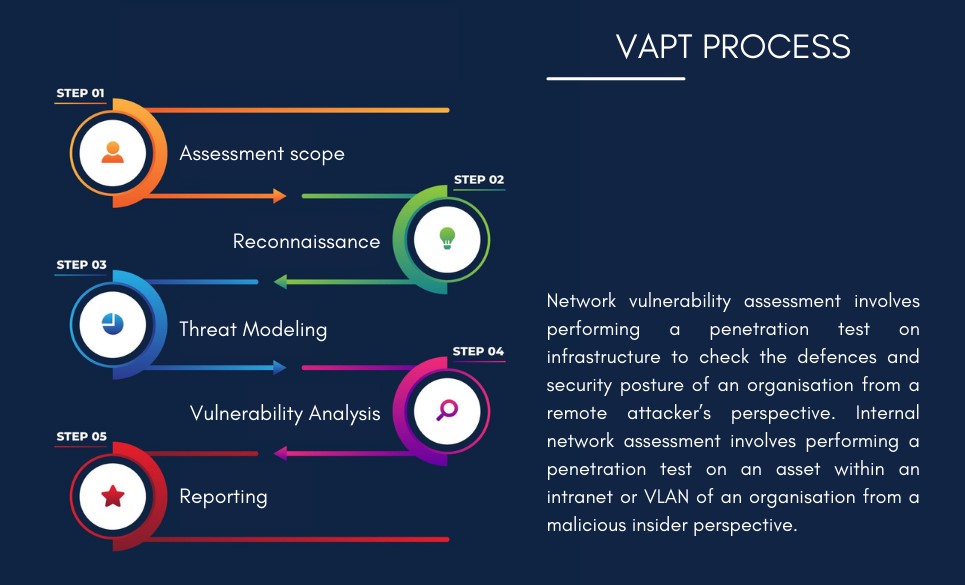
Network vulnerability assessment involves performing a penetration test on infrastructure to check the defences and security posture of an organisation from a remote attacker’s perspective. Internal network assessment involves performing a penetration test on an asset within an intranet or VLAN of an organisation from a malicious insider perspective.
What do you get?




End-to-End Assessment
Budget-friendly
Comprehensive Report
Extended Support
A unique blend of manual and automated network vulnerability assessment, as we believe in a hybrid approach for deeper and broader coverage of scope.
A flexible model of penetration testing that fits your business and budgeting requirements
Comprehensive report that elaborates the network vulnerabilities for both business and technical audiences.
Extended support from our team of experts to help you evaluate and fix the issues in a timely manner.
What do you get?

End-to-End Assessment
A unique blend of manual and automated network vulnerability assessment, as we believe in a hybrid approach for deeper and broader coverage of scope.

Budget-friendly
A flexible model of penetration testing that fits your business and budgeting requirements

Comprehensive Report
Comprehensive report that elaborates the network vulnerabilities for both business and technical audiences.

Extended Support
Extended support from our team of experts to help you evaluate and fix the issues in a timely manner.
What is VAPT?
VAPT stands for Vulnerability Assessment & Penetration Testing. It is security testing to identify security vulnerabilities in an application, network, endpoint, and cloud. Both the Vulnerability Assessment and Penetration Testing have unique strengths and are often collectively done to achieve complete analysis. Vulnerability Assessment scans digital assets and notifies organizations about pre-existing flaws, and penetration test exploits the vulnerabilities in the system & determines the security gaps.
Why would your organization need VAPT?
Vulnerabilities exist in all levels of a computing system (on-premise and cloud) regardless of the organization’s size. There’s a big misconception that cyber attackers spare small and medium-sized businesses. But this is far from reality. As the security of small businesses is usually relaxed, attackers incline towards them. Organizations often say they don’t require vulnerability risk assessments because they’re small. But this false belief could prove very costly for a business, big or small – SME or MNC. The security loopholes in your IT infrastructure are as follows:


Strengthen your defenses with TE VAPT
- Identify The Security Loopholes
- Improve Cyber Resilience
- Avoid Data Breaches
- Inspect Network Defence System
- Protect Organizational Data
- Comply with Security Standards

How It Works

Reconnaissance
This is the first phase of VAPT, in which an attacker uses tools to identify live hosts on a network.
The goal during this stage is to map out what devices are running and discover all active IP addresses that can be reached from outside the organization’s perimeter. It also includes mapping internal networks, finding sensitive data being transmitted over public networks, and finding servers with vulnerabilities that can be exploited.
Build Test Cases
The second phase of VAPT is where the actual security testing takes place. Test cases are created that highlight known vulnerabilities and how attackers can exploit them to gain unauthorized access to an organization’s IT environment.
Here, the goal is to find gaps in existing defenses or poorly configured systems so they can be remediated before an actual security incident occurs.
Deploy Scanners
The third phase of VAPT is where scanners run the test cases and identify vulnerabilities. It allows for a more thorough analysis than simply identifying vulnerabilities through manual testing.
Once all identified weaknesses have been confirmed, an organization’s security team can prioritize which issues need to be addressed first based on their impact level in mitigating the organization’s overall risk exposure.
Manual Penetration Testing
The fourth phase of VAPT is where penetration testing occurs, which includes manual exploitation activities that are used to validate the identified vulnerabilities are real and can be exploited by attackers. This stage further validates how an attacker could use these weaknesses to access critical systems and data.
As part of this phase, additional test cases are created so that security teams can continue to prioritize the issues identified in earlier stages based on their impact level within an organization’s overall risk exposure.
Report Generation
In the final stage of VAPT, a report containing all findings from previous steps is generated for distribution to senior management. It includes a summary of findings and recommendations to help the organization prioritize addressing identified vulnerabilities.
Final Thoughts
As you can see, there are many benefits to choosing VAPT services. It is worth it for businesses of any size to take the time and evaluate all their options carefully before deciding on this important purchase. If you have questions or need help, please contact us today.
We look forward to hearing from you soon.
About Technology Experts International
Technology Experts International is a leading provider of VAPT services, helping organizations identify their security posture to make informed decisions about their technology deployments. Contact us today for more information on our VAPT services or to schedule your free security assessment.
About us
Our goal: Top three worldwide Systems Integrator, offering innovative Technology Services, Digital Solutions, and Products
Get in Touch
- Unit 2&3, Howards Nursery Plummers Plain Horsham, RH13 6NX
- admin@te-international.com
- +44 0787939 7772
Insights






About us
Our goal: Top three worldwide Systems Integrator, offering innovative Technology Services, Digital Solutions, and Products
Get in Touch
- Unit 2&3, Howards Nursery Plummers Plain Horsham, RH13 6NX
- admin@te-international.com
- +44 0787939 7772
